Cybersecurity Governance Plan
Task: Strengthening Cybersecurity Governance: A Management Plan for Resilience
By Reynold W. Obuyekha
M.S. Cybersecurity, 2025
In today’s threat-heavy digital environment, having the right tools is not enough - you need the right people, policies, and preparation. This project involved developing a comprehensive cybersecurity management plan focused on improving governance, risk handling, and regulatory alignment for a mid-sized, security-challenged organization.
Key Gaps Identified
The initial assessment revealed several foundational issues:
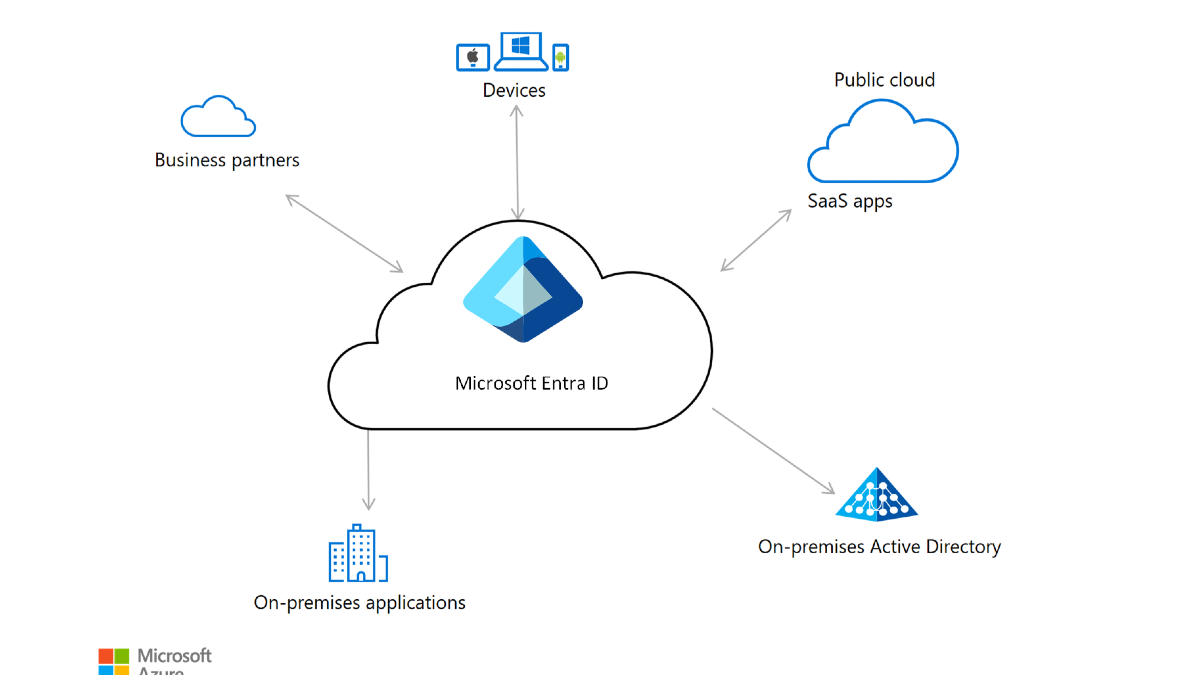
- - No alignment with compliance frameworks such as PCI DSS, GDPR, and NIST.
- - Only 10% of employees trained in cybersecurity via ad hoc efforts.
- - Understaffed security functions with unclear IR and GRC responsibilities.
- - Weak incident response planning and an incomplete business continuity strategy.
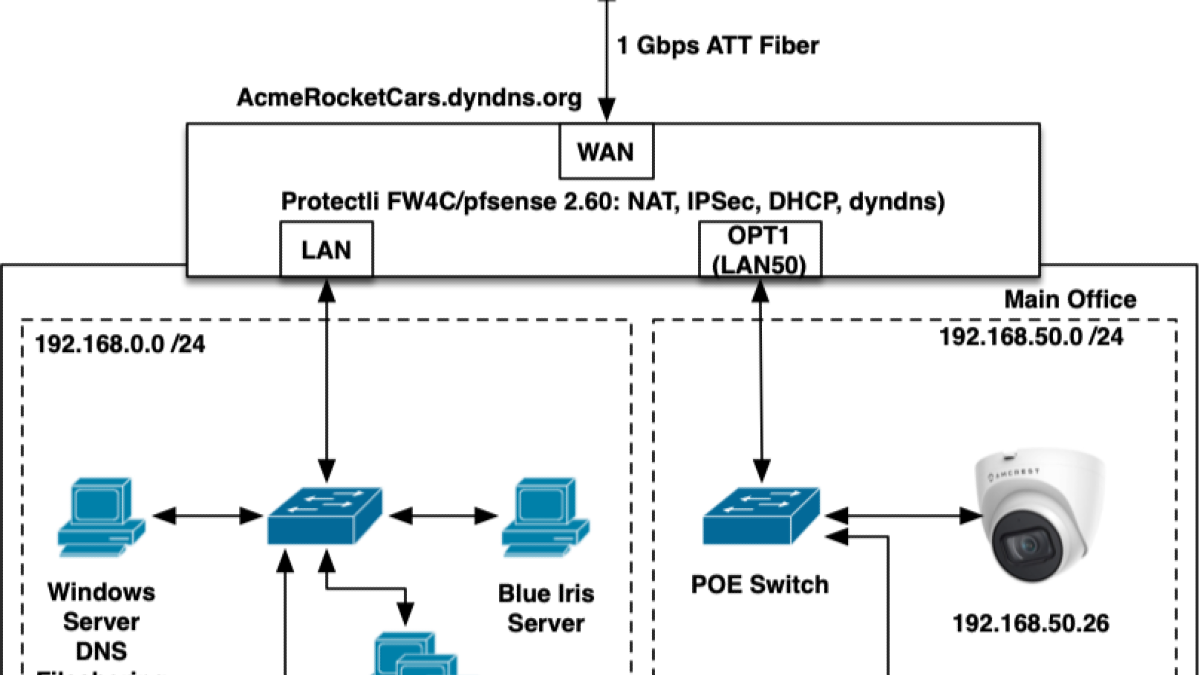
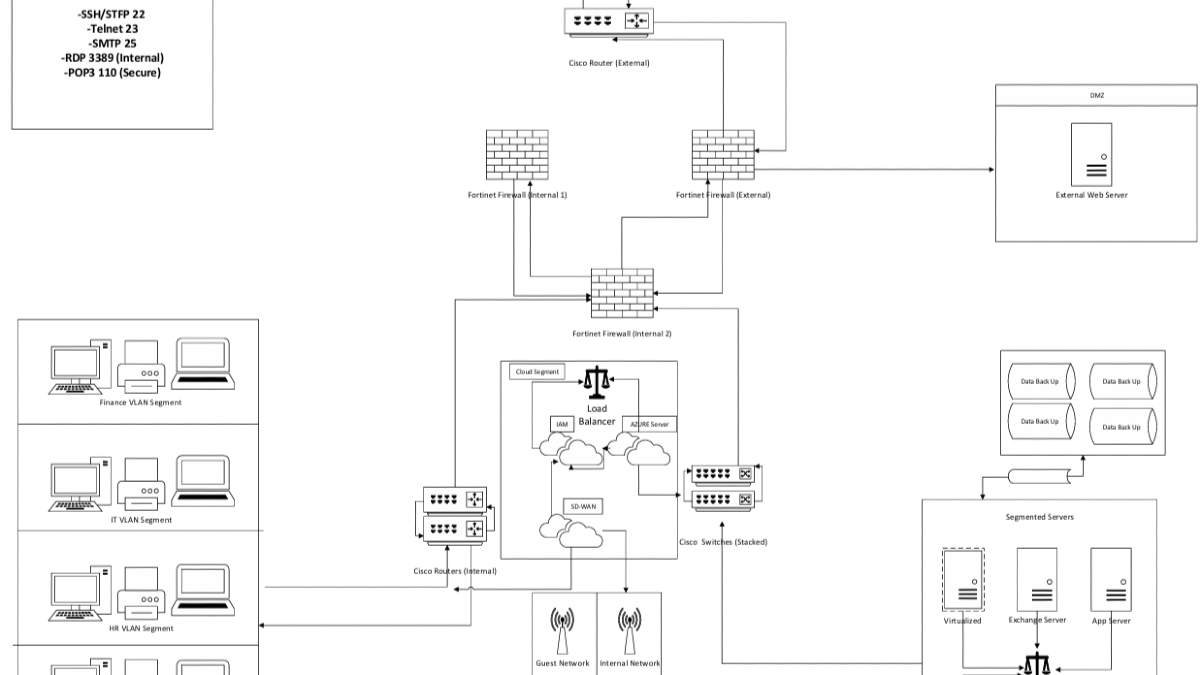
- - Lack of network segmentation, outdated policies, and vulnerable physical sites.
What I Proposed
Using the NIST SP 800 series, PCI DSS, and the NICE Cybersecurity Workforce Framework, I designed a set of layered mitigation strategies:
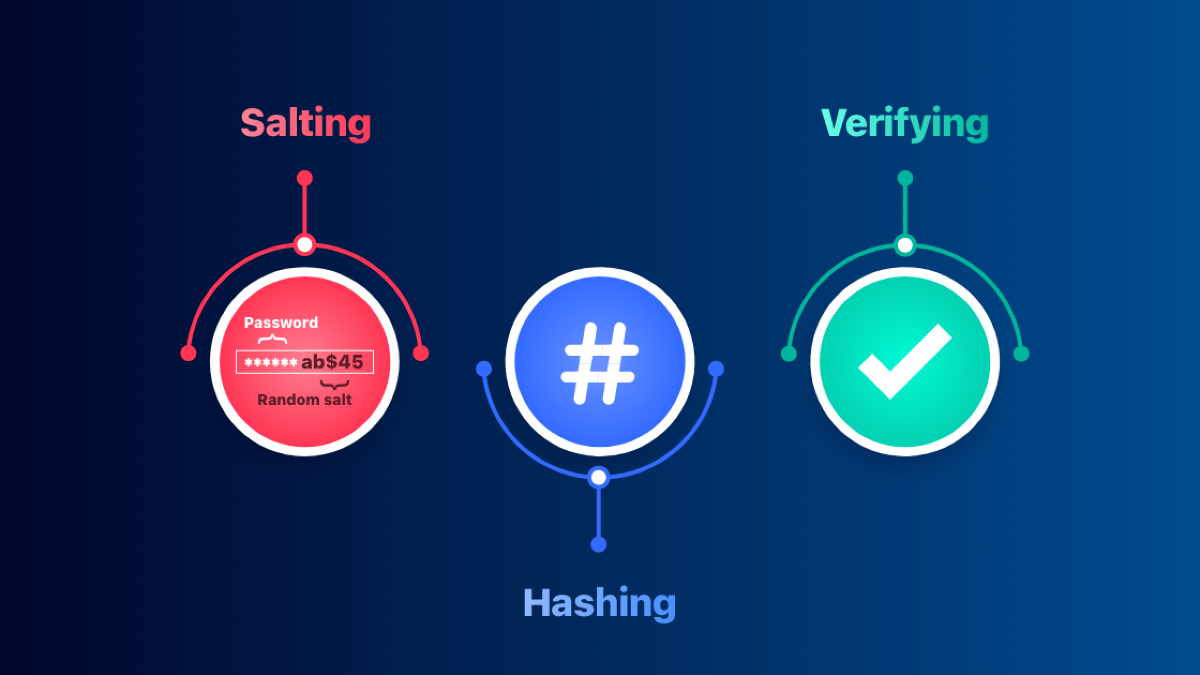
- - Policy overhaul to enforce secure practices for passwords, BYOD, and PII handling.
- - Full incident response lifecycle defined - Preparation, Detection, Containment, Recovery, and Post-Incident Review.
- - New roles added, including Privacy Compliance Manager, Cybersecurity Instructor, and Policy Manager, to support organizational maturity.
- - Cybersecurity awareness program launched with role-based training, phishing simulations, and interactive learning modules.
- - Business continuity plan updated to include location-specific natural disaster risks and IT resilience playbooks.
Threats Addressed
The plan addressed both physical threats (e.g., tailgating, device theft, natural disasters) and logical threats (e.g., phishing, insecure segmentation, insider threats). Security controls and training recommendations were tailored to each vector, ensuring layered protection across people, process, and technology.
Compliance and Policy Development
New policies were drafted in accordance with:
- - NIST 800-61 & 800-50 for incident handling and awareness.
- - PCI DSS for strong password and cardholder data protection.
- - GDPR for personal data governance, applying the 7 core privacy principles.
- - NIST 800-124 for securing mobile devices in BYOD environments.
Major Takeaways
This project reinforced that mature cybersecurity starts with management. A resilient security posture isn’t just built on firewalls and tools - but on clearly defined responsibilities, tested procedures, and empowered people. By aligning with industry frameworks and addressing the real-world needs of the business, the proposed plan turned a vulnerable organization into a prepared one.