Secure Network Design Post-Merger
Task: Building a Resilient Future: Secure Network Design Post-Merger
By: Reynold W. Obuyekha
M.S. Cybersecurity, 2025
When two companies merge, network security isn't just a checkbox, it’s a foundational priority. In this project, I was tasked with evaluating and redesigning the infrastructure of Company A and Company B, both of which faced significant cybersecurity and operational risks. My goal was to create a secure, scalable, and compliant network design that could support business continuity and regulatory mandates moving forward.
The Problem: Fragmented, Vulnerable, and Outdated network systems
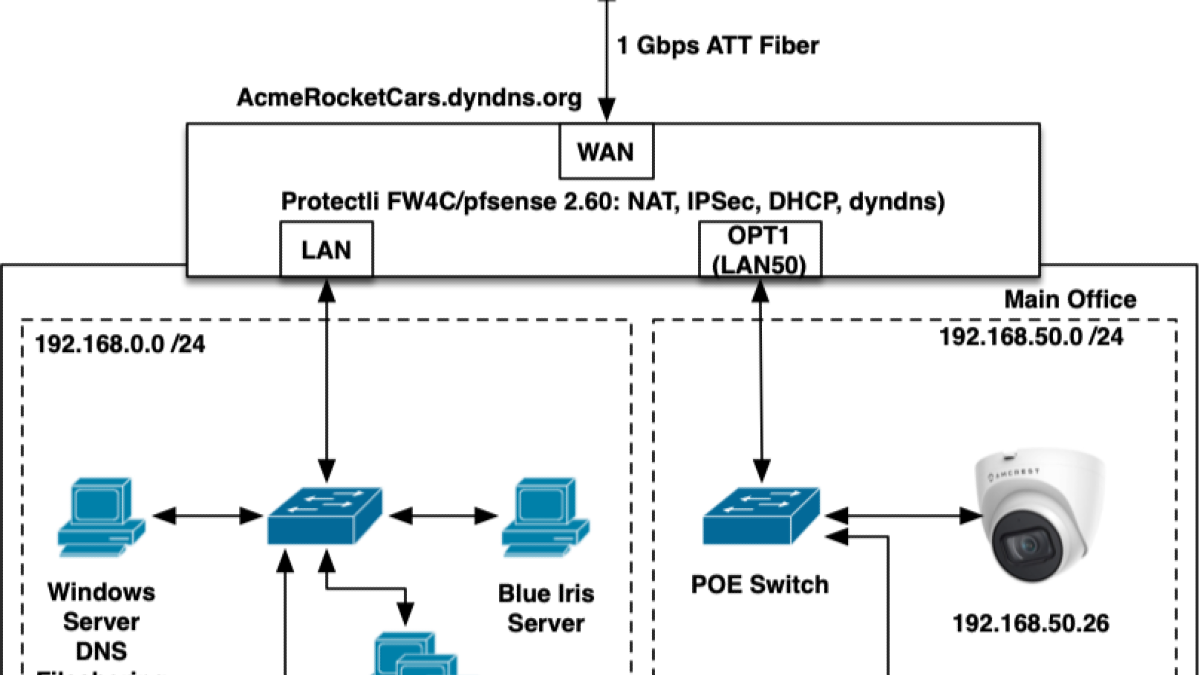
Company A suffered from weak internal segmentation and a single firewall protecting the entire network. Critical infrastructure lacked redundancy, backups were nonexistent, and everything depended on isolated hardware creating a single point of failure.
Company B, on the other hand, had performance issues tied to misconfigured subnets and numerous open ports. It also leaned heavily on on-prem infrastructure, which created high risks for scalability, ransomware resilience, and cloud migration costs. There was also no enterprise-wide enforcement of Multi-Factor Authentication (MFA), opening the door to credential-based attacks.
My Approach: Holistic Network Re-Architecture
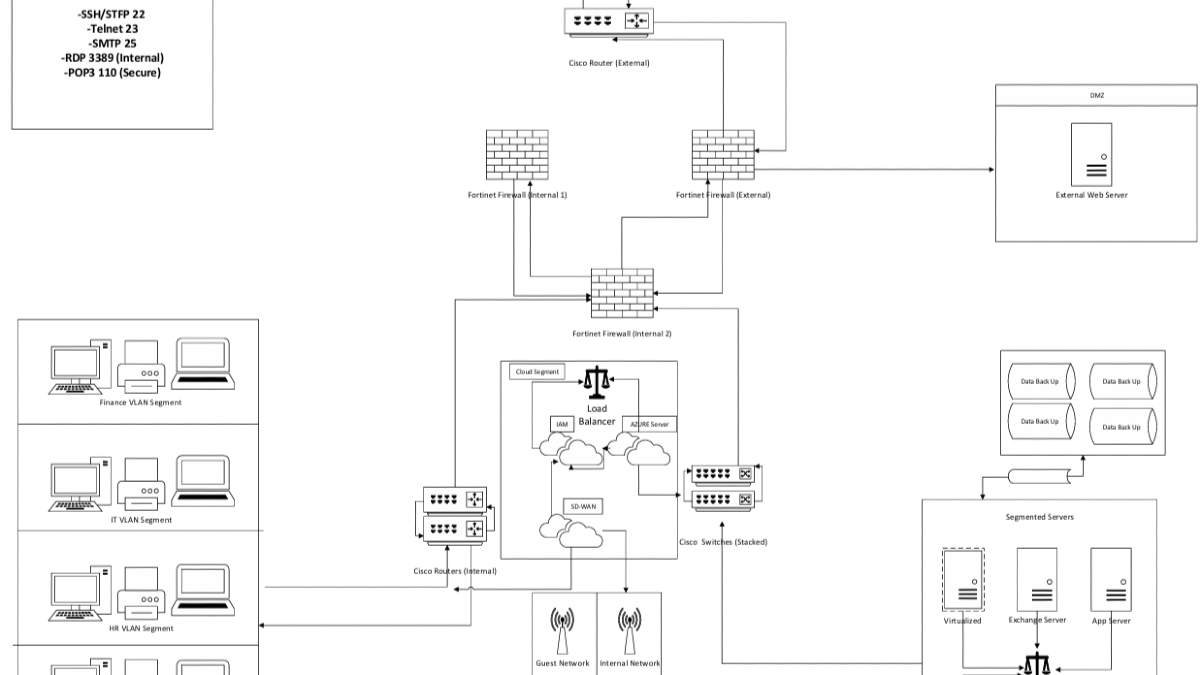
After a comprehensive risk and vulnerability assessment, I designed a hybrid network model to meet operational needs, reduce exposure, and support compliance across financial and regulatory domains.
Key steps included:
- - Segmenting the network using VLANs to isolate traffic by department and purpose.
- - Implementing IAM and MFA to protect access points and enforce least privilege.
- - Deploying SD-WAN and NGFWs to improve performance and detect threats in real-time.
- - Integrating cloud-based services like Azure IAM and storage for redundancy, resilience, and scale.
Each component was mapped to the OSI and TCP/IP models, ensuring the design met both architectural and security best practices.
Major Issue: Budget-Conscious Upgrades with Business Value
A total of $40,515.48 was budgeted to add firewalls, load balancers, access points, cloud services, and licenses -while strategically repurposing existing hardware like virtualized servers and retiring legacy equipment. This approach reduced waste and kept the transformation lean, agile, and cost-effective.
Compliance: Meeting Compliance with PCI DSS and SOX
Company A, now dealing with sensitive financial data (bank cards and investment services), required strong alignment with PCI DSS. Company B's financial reporting required SOX compliance. My design addressed both by ensuring:
- - Encrypted transmission and storage of sensitive data (AES-128+)
- - Strict access control via role-based policies
- - Audit trails and logs for system and user activity
These controls help ensure not only data confidentiality but also operational integrity and legal accountability.
Addressing Emerging Threats
Merging environments always carry inherited risks, such as dormant malware and insider threats. I recommended:
- - A comprehensive post-merger security audit
- - NDAs and internal security training for all staff
- - Continuous monitoring with a central SIEM solution
This helps the organization reduce exposure from unknown vulnerabilities and human factors-often the most exploited in a modern threat landscape.
Key Takeaways
This project solidified my belief that security architecture is not just about firewalls or encryption-it’s about understanding the business, aligning solutions with strategy, and designing for resilience at scale. With the right mix of on-premise control and cloud-based flexibility, businesses can move fast without compromising trust, compliance, or security.